Ensuring that your endpoint and server protection is correctly configured is one of the most important things you can do for your organization’s security.
Add a web server protection (WAF) rule With WAF rules, you can protect web applications from attacks and data leakage by filtering HTTP traffic. You configure a WAF rule for an IP address assigned to a network interface, a port, and one or more domain names. XG Firewall matches traffic based on the IP address assigned to the interface.
Sophos Web Server Protection Policy
- Sophos Anti-Virus for Mac OS X, Sophos Anti-Virus for Windows 2000+, Sophos Firewall, Sophos Security Management Appliance, Sophos UTM, Sophos Web Appliance, Sophos Web Appliance Virtual What to do If, in your opinion that the site alert is incorrect, follow the below steps to request a reassessment. Sophos indicates that the site contains malware.
- This article explains the basics of configuring a Sophos XG Firewall with the Web Application Firewall (WAF) feature.
- Sophos Central Sophos Mobile XG Firewall. Web Server Protection: DoS Protection The WAF, based on Apache reverse proxy, if enabled, can become a target for App.
This article will give you some quick tips and links to resources so you can get the most out of your Sophos protection.
Getting started
In Sophos Central policies are used to apply protection settings such as specific exploit preventions, application control, and peripheral control. Policies can apply to endpoints, servers, users or groups depending on how you want to set things up. How to create a policy.
Application Control
Controls which applications should be blocked. For example, uTorrent and Steam games.
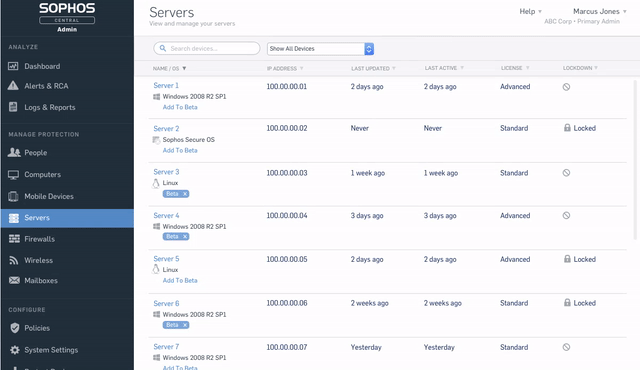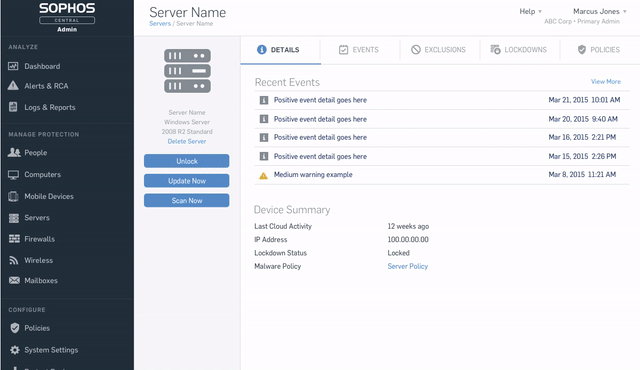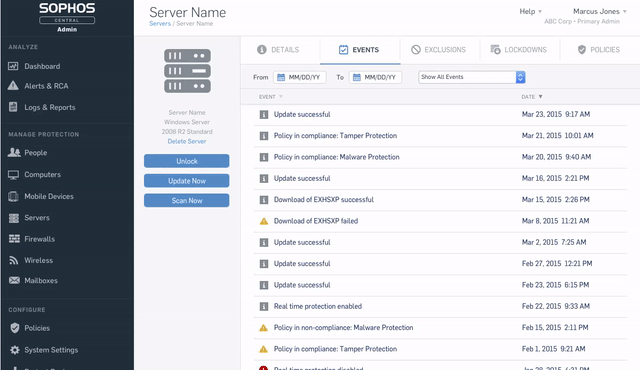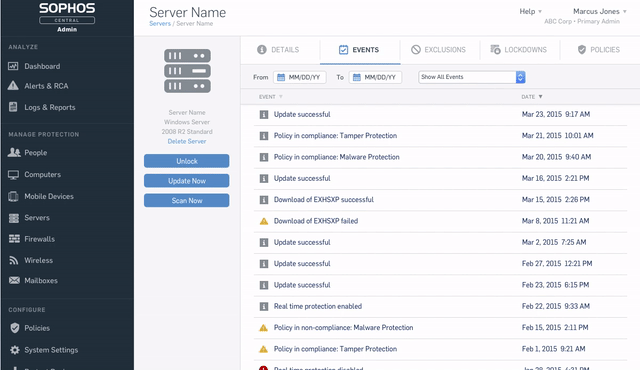
Endpoint setup | Server setup
Data Loss Prevention
Stops specific file types or content in a file from being transferred from a device. For example, stop files containing account numbers being sent from a device.
Endpoint setup | Server setup
Windows Firewall
Blocks inbound connections from specific domains or networks. For example, stopping all private networks accessing a device.
Endpoint setup | Server setup
Peripheral Control
Controls what can be plugged into a device. For example, blocking USB sticks and optical drives.
Endpoint setup | Server setup
Threat Protection
Configures protection features. We strongly suggest always using Sophos recommended settings.
Endpoint setup | Server setup
Update Management
Schedules updates to a specific time. For example, setting them after office hours.
Endpoint setup | Server setup
Web Control
Sophos Web Server Protection
Stops users downloading risky files or accessing inappropriate websites. For example, block .exe file downloads.
Endpoint setup | Server setup
File Integrity Monitoring (Server only)
Monitors important files and folders for signs of tampering. For example, critical Windows directories or key programs.
How to set one up.
Tamper Protection
Tamper protection stops unauthorized users and types of malware from uninstalling Sophos protection. You should always have it enabled. Learn more.
Do I need to log in and check for alerts?
Users often ask how often they should log in to check for alerts and actions. The good news is that Sophos Central automatically emails admins when there is an event requiring their attention. Here’s how to configure alerts.

Check your security posture with EDR
Endpoint Detection and Response (EDR) is a powerful tool to help you find threats across your network. It’s easy to get started by checking the list of the most suspicious potential threats for investigation in your organization.
We give you curated threat intelligence so you can quickly decide whether a potential threat needs taking care of. Watch the EDR how-to videos.
More information
With IPS policies, you can prevent network attacks using rules. The firewall enforces the actions specified in the rules and logs the corresponding events. The set of default policies prevents network attacks for several common types of traffic. You can create custom policies with rules that meet your traffic requirements.

- To add a policy, click Add and type a name. Then, you can clone the rules from an existing policy.
- To add rules to a policy, click for the policy you want to edit, and then click Add.
IPS policy rules
Rules specify signatures and an action. The firewall matches signatures with traffic patterns and takes the action specified in the rule. The action specified for the rule overrides the action recommended by the signature.
IPS signatures
Signatures identify threats and specify a recommended action to take when the firewall encounters matching traffic. Signatures are specific to applications, services, or platforms. The firewall includes predefined signatures and you also can create custom signatures.
.jpg?width=600&name=Sophos XG Firewall Licensing Model (1).jpg)
- SID
- ID of the IPS signature.
- Category
- Category of IPS signature.
- Severity
- Degree of threat severity.
- Platform
- Signatures that apply to specific platforms (for example, Microsoft Windows).
- Target
- Client or server-based signatures.
- Recommended action
- Action recommended by the firewall when traffic matches the signature.
